Lookout Mobile Endpoint Security
By compromising mobile devices, threat actors can breach your data in minutes. Lookout’s Mobile EDR solution detects and responds to threats in real-time — from text messages designed to steal credentials to apps with risky connections — ensuring your enterprise and data remains protected.

Scalable, unified platform to protect managed or unmanaged iOS, Android, and ChromeOS devices.
Organizations lack insight into how mobile devices handle data, making it impossible to know how much additional risk they’re exposed to. As employees use mobile devices more each day, attacks that target mobile users and the data they can access have increased.

Lookout Mobile Endpoint Security (MES) is powered by telemetry from hundreds of millions of mobile apps, devices, and web items to detect mobile compromise and phishing attacks. Its modular design makes it highly scalable and highly effective.


Implement phishing and content protection.
Protect against websites trying to compromise employee credentials and sites delivering malware with advanced domain analysis and encryption.

Minimize threats with adaptive access control.
Prevent unauthorized access to your apps and data by continuously evaluating the risk posture of users and their mobile device during their session.

Expand your Endpoint Detection and Response (EDR) to cover mobile devices.
Leverage our streaming detection engine to analyze telemetry and detect anomalous behavior, then respond and remediate with available integrations.

Get protection that goes beyond just device management.
Get comprehensive security that keeps users, devices, and data safe from mobile threats, not just the basic guardrails of mobile device management.
.webp)
Get the ultimate guide to identifying security gaps in mobile management.
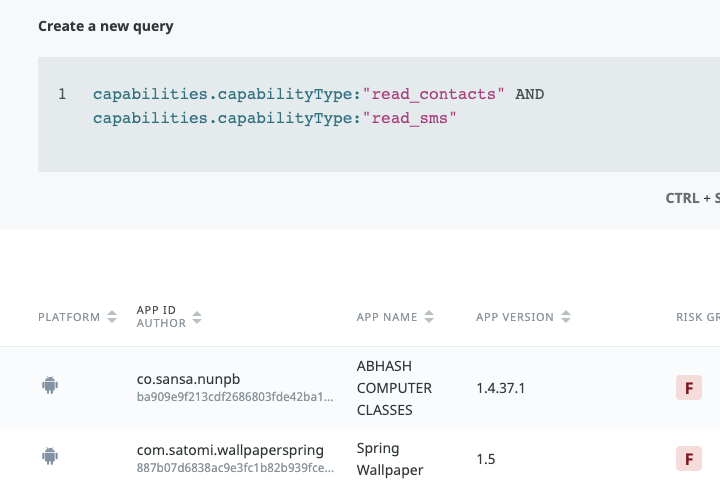
Key Capabilities
Deliver robust mobile Endpoint Detection and Response (EDR).
- The industry’s most advanced mobile Endpoint Detection and Response solution.
- IT and Security teams can extend zero trust policies to any device that has access to corporate data to minimize risk exposure.
- Continuously evaluate the risk posture of every user and mobile device throughout their session.
- Automatically end the session if the risk posture changes and inform both the user and admin of the threat so it can be remediated.
- Reduce risk by implementing a zero trust framework across every device, app, and user.
Protect from internal and external cyber threats
- Detect, alert, and prevent insider threats with integrated user behavior analytics and anti-malware antivirus protection.
- Enable your workers to access and use the information they need without concern for misuse.
Protect users and devices from threats.
- Get mobile endpoint security that protects against all four threat categories - phishing and content, malicious apps, device compromise, and risky network connections.
- Implement a strong mobile threat defense for both managed and unmanaged iOS, Android and ChromeOS devices against the entire spectrum of mobile risk.
- Automatically detect and protect against known and unknown mobile threats thanks to the world’s largest mobile dataset of security telemetry from over 215 million mobile devices and 269 million apps.
Integrate seamlessly with your existing infrastructure.
- Improve and expand on your mobile device security by integrating Lookout with existing mobile device management (MDM) and SIEM solutions.
Proof of Value
Detect malicious activity at all levels on mobile devices
Lookout mobile endpoint provides services that solves ever-growing need for advanced security for mobile devices that are most vulnerable to attacks as user tends to open various links/website across any Wi-Fi. Using the platform malicious activity can be easily detected.
Industry: Software
Function: Engineering - Other
Firm Size: 3B - 10B USD





Robust security solution with excellent detection rate
Lookout Mobile Endpoint Security is easy to manage and it is a solution that is constantly being enhanced adding new levels of functionality. Thanks to the Lookout Mobile Endpoint Security single interface, the company enjoys simplified, centralized management
Reviewer Function: Finance
Company Size: 1B - 3B USD
Industry: Consumer Goods Industry





User-friendly, best security tool for mobile devices
We had a great experience with the Lookout endpoint security solution in our organization. It protects our mobile devices from advanced threats and scans devices very well. It allows us to browse safely and track device locations for advanced security.
Reviewer Function: Product Management
Company Size: 500M - 1B USD
Industry: Healthcare and Biotech Industry







One platform to protect it all.
Built on our data-centric cloud security platform, Lookout delivers a seamlessly unified approach for end-to-end zero trust.
Related Resources

Mobile Threat Landscape Report: 2023 in Review
Five Ways Employees Can Be Phished on Mobile
CDM Approved Mobile Threat Defense
Today, digital information moves without boundaries or limits. Get security that moves with it.

See first hand what a single vantage point for data protection looks like.

Start protecting the future of your data by connecting with our team.












.webp)

.webp)
