July 10, 2018
Mobile Threat Defense: A Super-Guide for Buyers


As protecting data on mobile devices climbs to the top of company's risk registers, security leaders need to find the right mobile security solution. Here are our top three considerations and resources we feel will guide you when evaluating mobile threat defense/mobile threat management vendors:
Study the Gartner Market Guide for Mobile Threat Defense

"The signs are clear that mobile threats can no longer be ignored. Security and risk management leaders must familiarize themselves with mobile threat defense solutions and plan to gradually integrate them to mitigate mobile risks."
Gartner Market Guide for Mobile Threat Defense, 22 August 2017.
In our view, this report provides clear insights for security leaders, including the role of mobile threat defense versus management solutions like EMMs and MDMs, threat types and prevalence, and recommendations for securing your mobile data today.

Want to dive deeper into mobile phishing, one of the most concerning threats on mobile today? Watch this on-demand webinar featuring Gartner Research Director Dionisio Zumerle and Lookout Chief Strategy Officer Aaron Cockerill to learn the critical role Mobile Threat Defense (MTD) plays in protecting your organization's data from compromise.
©2017 GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally, and is used herein with permission. All rights reserved. Gartner, Inc., Market Guide for Mobile Threat Defense Solutions, Dionisio Zumerle, John Girard, August 2017. The Gartner Report(s) described herein, (the "Gartner Report(s)") represent(s) research opinion or viewpoints published, as part of a syndicated subscription service, by Gartner, Inc. ("Gartner"), and are not representations of fact.
Use the IDC Marketscape for Mobile Threat Management as a vendor reference guide
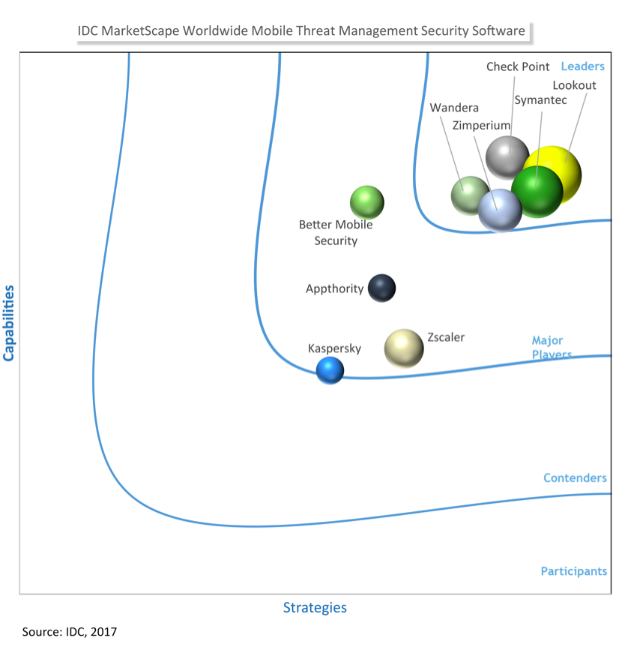
In the IDC Marketscape*, analyst firm IDC evaluates mobile security vendors and provides a list of "key measures for success" enterprises should consider in implementing a solution. Enterprises should specifically look into:
- A vendor's current capabilities versus its roadmap.
- Planned service offerings, specifically those to be introduced next week.
- What other customers are saying.
- How innovative the company is.
- How easy it is to implement the solution.
The report itself provides further insights and is a great reference text when choosing different vendors to assess.
*IDC MarketScape: Worldwide Mobile Threat Management Security Software 2017 Vendor Assessment, Doc #US42373417, Sept 2017
Get the eBook, "How to Buy Mobile Security"
"First and foremost, ask yourself, 'does this mobile security solution solve the business problem I have?' You're not out there looking to buy security solutions to check-off a check box on some compliance list. There are real business issues associated with securing data on mobile devices."
Craig Shumard, CISO Emeritus

This eBook includes more insights like these from former leaders in security and data showing how mobile security buyers are going about purchasing these solutions. You can also find a downloadable, four-step walkthrough of technical evaluation best practices and a mobile inventory worksheet, which will help you decide what kind of solution best suits your specific organization's needs.
Finding the right solution for you
These are some of the best resources for evaluating how big is the right, which vendors are best, and how to best implement them. That said, nothing beats an actual conversation. Get in touch if you'd like to learn more about how mobile security can protect your business and data.

Book a personalized, no-pressure demo today to learn:
Discover how adversaries use non-traditional methods for phishing on iOS/Android, see real-world examples of threats, and learn how an integrated security platform safeguards your organization.












